
Subject: Cyber Security I (KB I), Department of Telecommunications, Faculty of electrical engineering and computer science, VSB-TUO.
Name: Bc. Kryštof Šara (SAR0130)
Date of presentation: December 15, 2023
introduction
In the modern era, it is a standard to ensure HTTP over SSL/TLS layer (HTTPS) on any web page possible. However, the implementation of Public Key Infrastructure (PKI), such as getting the keys and certificates can be a problem, when using internal domain name systems and internal domains, that are not accessible from the Internet. For this scenario, one could generate self-signed certificates, that need to be imported to every single worker’s computer for the browser to provide the connection without issues.
Another approach could be using HTTP-only implementetaion on web servers, effectively providing simple and fast connections. On the other hand, it is possible to easily capture and find used credentials in unencrypted packets.
HyperText Transfer Protocol (HTTP)
As far a HTTP is concerned, it is an application-layer (ISO/OSI layer 7) protocol. It is mainly used for hypermedia (for example formatted text with images and links) distribution. It could also be used to stream chunks of data in terms of IPTV operation. It is a classic server-client protocol, where on the server side there is a WWW/web server, while on the client side there is, most commonly, a web browser. [7]
methods
The most important, and possibly most used HTTP methods are GET and POST methods. Those methods are generally a wrapper functions to differentiate between various type of HTTP request call types. Other methods are PUT, PATCH, OPTIONS, UPDATE, DELETE and some other very special methods. [1]
GET
GET method is basically used to retrieve information from server. If the server counterpart defined by request URI is a data-producing process, the produced data are returned instead. In the other case, the (source) text is returned. [7]
POST
POST method is meant to be used with some encapsulated data reuests for resources. One way of usage is to post/append a new message/item/entity to the remote server, while attaching the data in the form of request payload. [7]
VPN
Virual private networks (VPN) are a special subset of networks, interconnected through the public Internet. Those networks basically act like apparent local area networks, while still being securely accesible from elsewhere around the globe (so-called road warrior type of implementation for travelling businessmen. [8]
WireGuard protocol
WireGuard is ISO/OSI Layer3 network tunnelling software, designed primarily as kernel module for GNU/Linux systems (introduced in 5.6 kernel). Compared to IPSec and still widely favourite OpenVPN technologies, WireGuard offers better performance, security, and simplicity to use. An implementation of fundamental secure tunnels deals with peer’s public key and source IP address. Data are authenticated and encrypted using ChaCha20Poly1305, and encapsulated in UDP datagrams. The simplicity can be seen in a generic Linux implementation, which is possible to perform in less than 4000 lines of code (great advantage to OpenVPN implementation). [6]
tcpdump
 Fig. 1: Official tcpdump logo.
Fig. 1: Official tcpdump logo.
tcpdump tools is a powerful packet analyzer for command-line interface (CLI). tcpdump can also capture packets, that is the very common purpose of tool’s usage.
[3]
[4]
| |
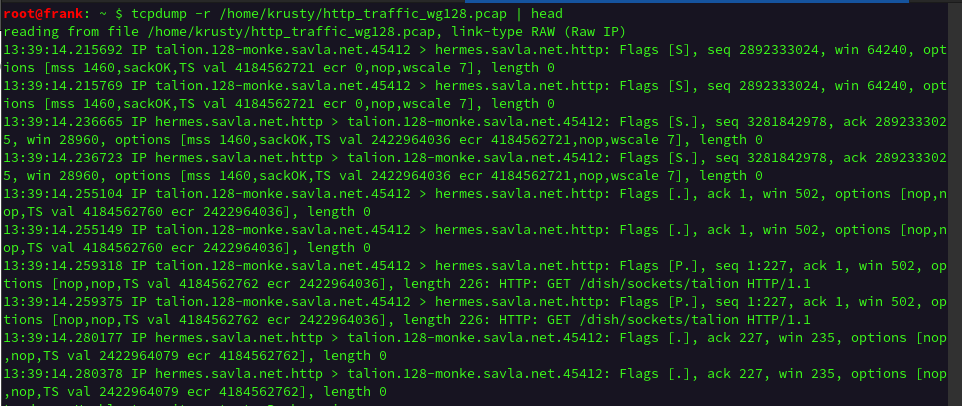 Fig. 2: Trimmed output of captured packets in
Fig. 2: Trimmed output of captured packets in .pcap file using tcpdump in CLI.
wireshark
 Fig. 3: Official Wireshark logo.
Fig. 3: Official Wireshark logo.
Wireshark is a free and open-source packet analysis tool. It could be used both for capturing packets, as well as the online/offline analysing of the captured packets. Those packets are then shown in mostly human readable structured format. This way one could analyze various types of network protocols. It is meant to work on multiple platforms like Windows, GNU/Linux, BSD and many more. [1] [5]
software repositories
tcpdump is relatively common GNU/Linux tool. It is also very common, that this tool is already a part of the Linux distribution package.
To install both packages, one could simply execute system package manager’s install command:
| |
traffic capturing and analysis
To capture the credentials pair, we need to use some basic HTTP site as a generic portal entrypoint. Credentials for authentication are commonly sent using HTTP POST requests.
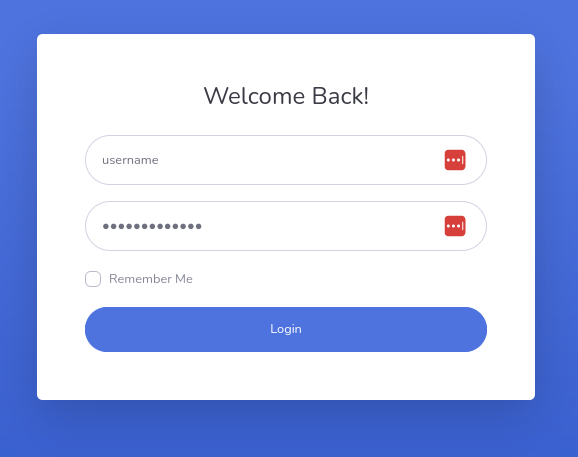 Fig. 4: Simple HTTP site’s HTML form with entered credentials.
Fig. 4: Simple HTTP site’s HTML form with entered credentials.
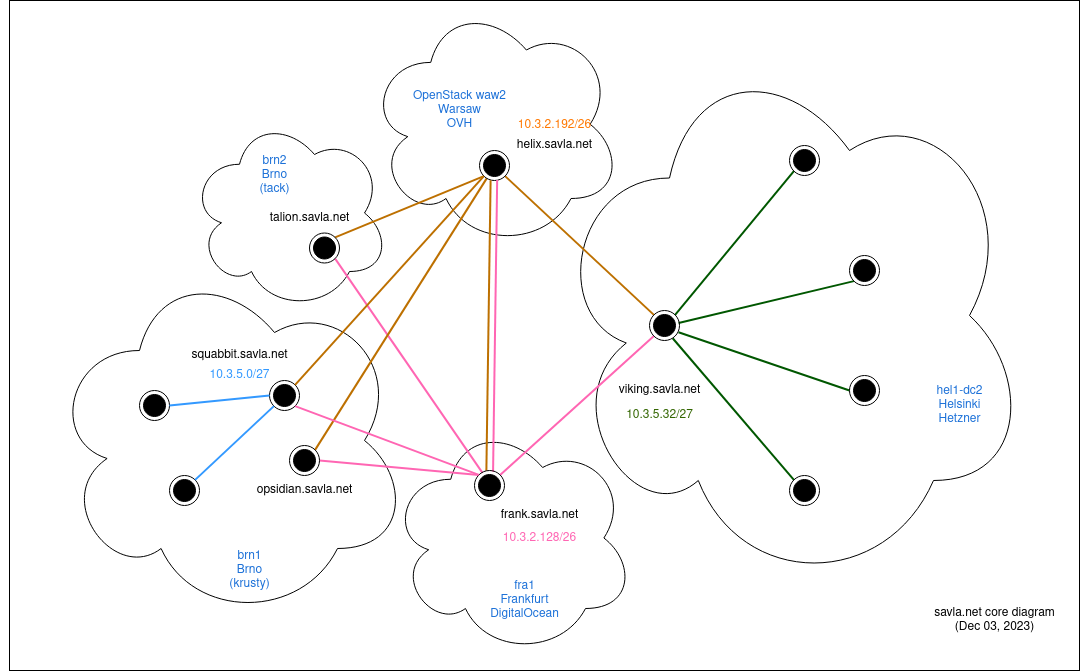 Fig. 5: Network topology diagram. The chosen concentrator server is named frank (pictured at the bottom of diagram).
Fig. 5: Network topology diagram. The chosen concentrator server is named frank (pictured at the bottom of diagram).
setting up the capturer
First, it is necessary to set up tcpdump tool on VPN concentrator to catch the HTTP traffic. For this procedure, special permissions are need to be applied. One has to be able to raise privileges using sudo or by logging in as root account.
[2]
| |
| |
The .pcap file is a special type of file, that indicates it’s containing catptured packets and that it could be open for further analysiss in tools such as Wireshark.
To catch password or any credential from a HTML form, we need to use some intranet website with those components implemented in the site.
getting the file
To transfer the file over secure copy (scp), we could simple type:
| |
wireshark
Next step in analysis is opening that .pcap file in Wireshark tool, simply via File => Open in the menu topbar, and by selecting the file in dialog window.
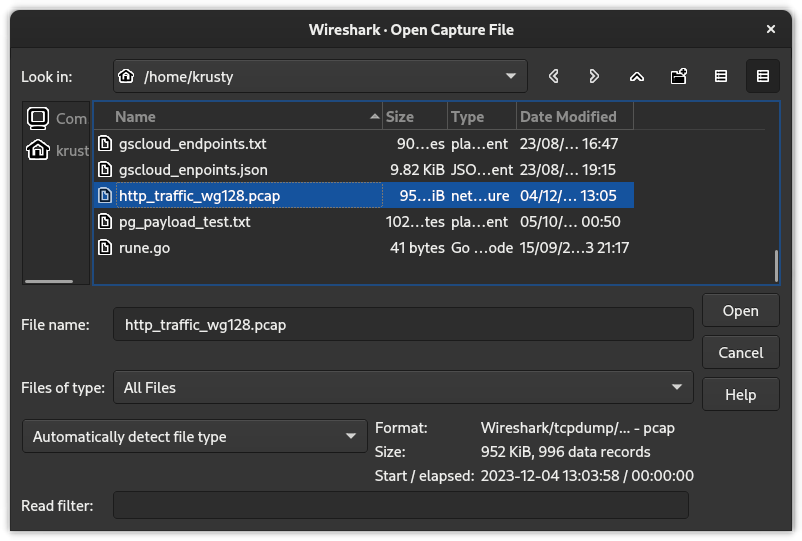 Fig. 6: Opening a file in Wireshark using the program dialog window.
Fig. 6: Opening a file in Wireshark using the program dialog window.
As soon as the file is loaded, we can filter out HTTP-only packets by typing http in the filter bar. This procedure will give us a list of HTTP packets captured only.
[1]
Furthermore, we can even select a specific HTTP method using this syntax: [1]
| |
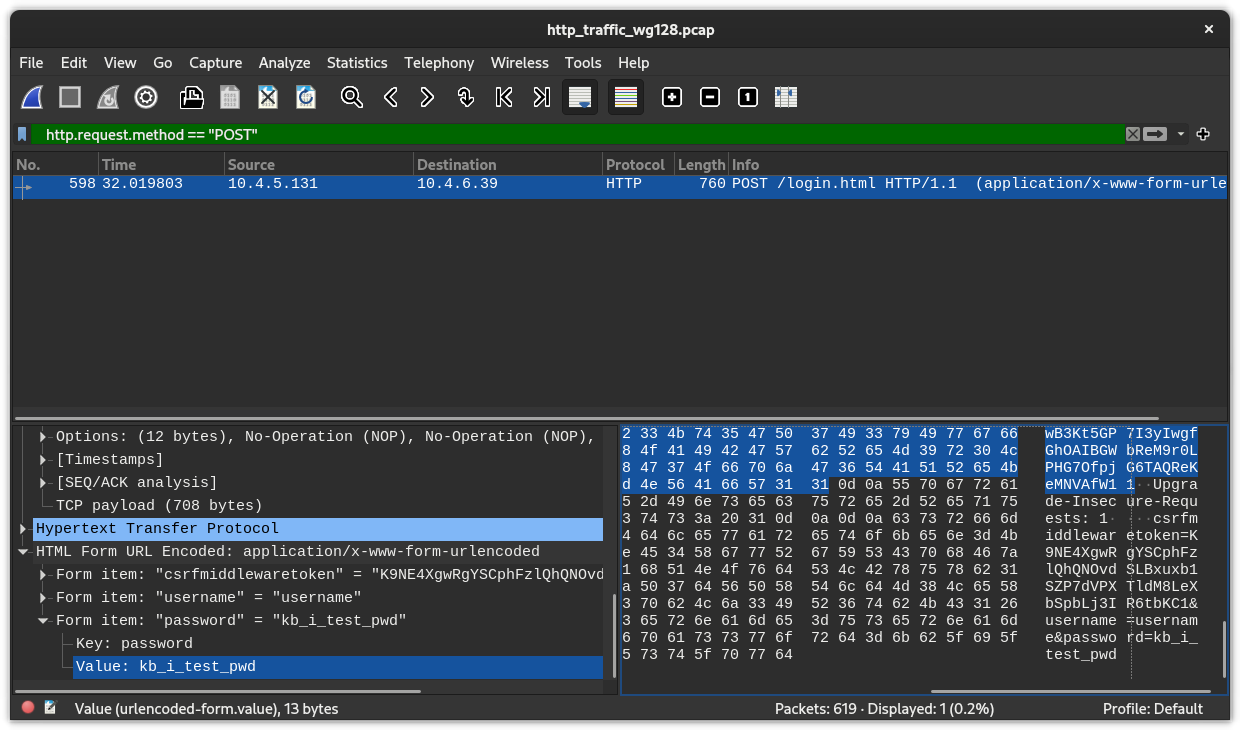 Fig. 7: Filtering out the HTTP POST requests to decode username and password fields from the HTML form.
Fig. 7: Filtering out the HTTP POST requests to decode username and password fields from the HTML form.
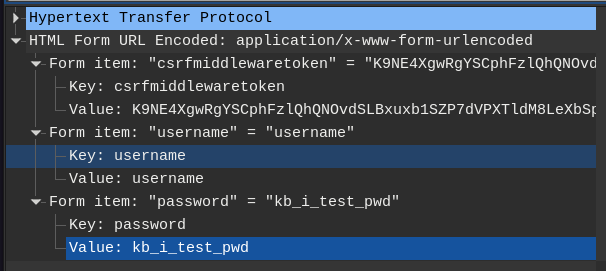 Fig. 8: Detail of HTTP packet parsed structure in Wireshark.
Fig. 8: Detail of HTTP packet parsed structure in Wireshark.
conclusion
Due to the simplicity of packet capturing on the side of VPN concetrator server, it is vital to enforce strict linux user autorization (by carefully set up sudoers file for example), as well as the access to server itself. Another layer of security can be done on the level of SSH server — to enforce using public keys authentication, and by disabling root login.
When WireGuard protocol is used on a non-primary network interface, everything that is oushed through the primary interface is then seen as encrypted and therefore couldn’t be read for passwords.
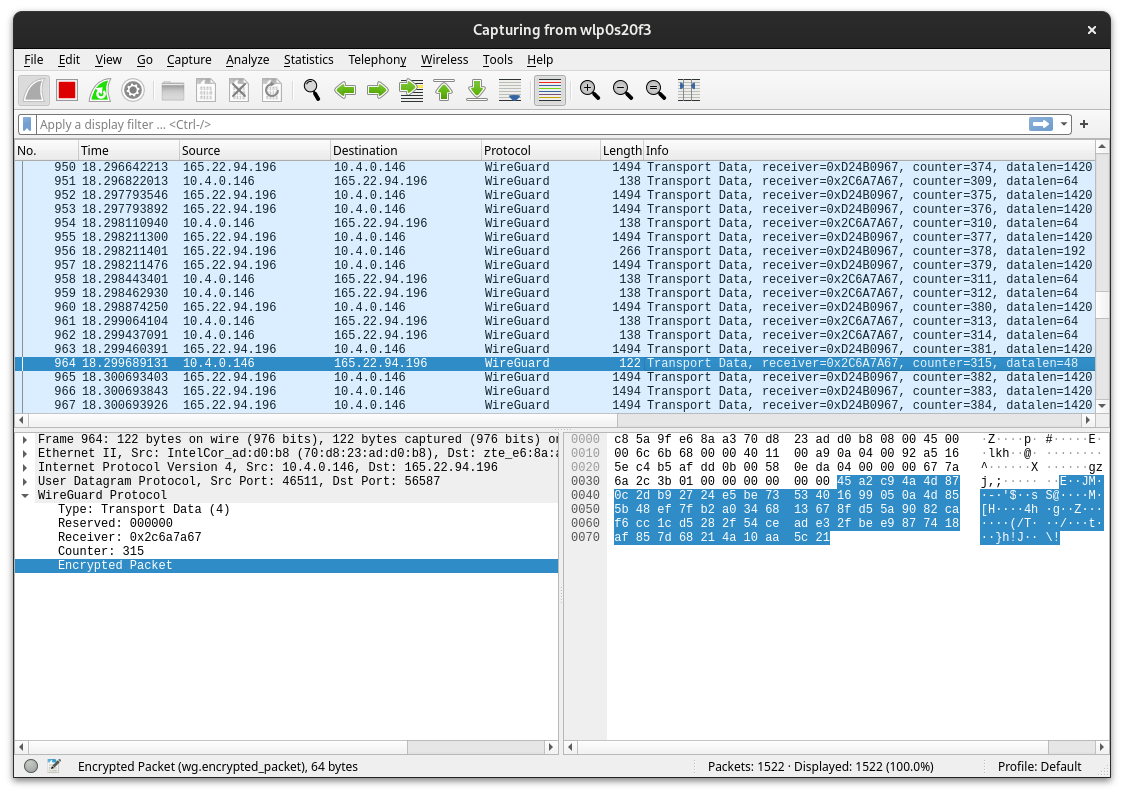 Fig. 9: Captured encrypted WireGuard-encapsulated packets detail.
Fig. 9: Captured encrypted WireGuard-encapsulated packets detail.
references
| ref number | ref content |
|---|---|
| [1] | https://www.geeksforgeeks.org/sniffing-of-login-credential-or-password-capturing-in-wireshark/ |
| [2] | https://stackoverflow.com/questions/39012132/how-to-capture-only-http-with-tcpdump-with-linux |
| [3] | https://www.tcpdump.org/manpages/tcpdump.1.html |
| [4] | https://www.tcpdump.org/index.html |
| [5] | https://www.wireshark.org/about.html |
| [6] | https://www.wireguard.com/papers/wireguard.pdf |
| [7] | https://datatracker.ietf.org/doc/html/rfc2616 |
| [8] | PUŽMANOVÁ, Rita. TCP/IP v kostce. 2., upr. a rozš. vyd. České Budějovice: Kopp, 2009. ISBN 978-80-7232-388-3 (CZ). |